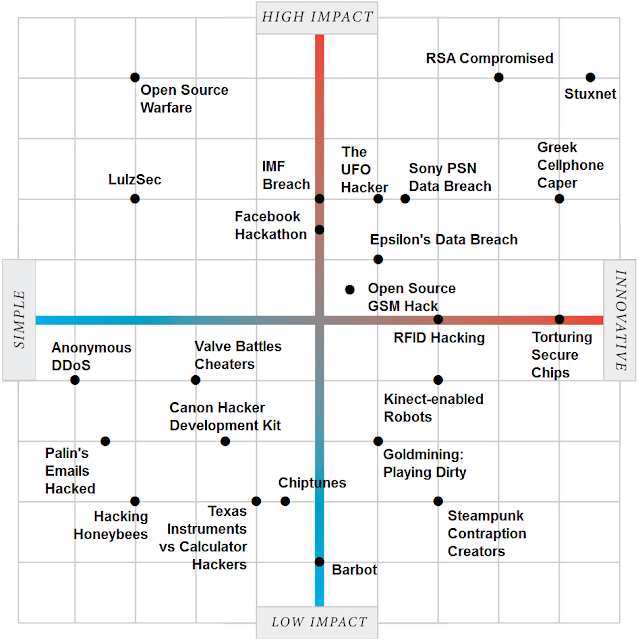
Most trusted companies for privacy
Updated: 2011-07-31 15:55:25
Ponemon Institute is releasing our annual Most Trusted Companies for Privacy study this coming week. This is the eighth year that we conducted a U
 Not all insurance policies are created equal and organizations should check their policies before a data breach to see if they are covered. In the case of Sony, perhaps not. - Recent high-profile cyber-attacks have renewed interest in
cyber-insurance as CEOs worry about covering the cost of a data breach
if, or when, they get attacked. However, the policies they are buying
may not help them in case of a large-scale breach.
Sony is discovering this the hard way a...
Not all insurance policies are created equal and organizations should check their policies before a data breach to see if they are covered. In the case of Sony, perhaps not. - Recent high-profile cyber-attacks have renewed interest in
cyber-insurance as CEOs worry about covering the cost of a data breach
if, or when, they get attacked. However, the policies they are buying
may not help them in case of a large-scale breach.
Sony is discovering this the hard way a... The amount of personal and professional information posted on social networks means it's increasingly easier for criminals to create a detailed profile of their victims. - Social networks provide spammers with plenty of opportunities to scam
users in new and more effective ways, a security expert said.
Social networks have become ubiquitous, with more than 500 million users on
Facebook, 100 million on LinkedIn and a reported 200 million users on Twitter.
Google cl...
The amount of personal and professional information posted on social networks means it's increasingly easier for criminals to create a detailed profile of their victims. - Social networks provide spammers with plenty of opportunities to scam
users in new and more effective ways, a security expert said.
Social networks have become ubiquitous, with more than 500 million users on
Facebook, 100 million on LinkedIn and a reported 200 million users on Twitter.
Google cl... Anonymous continued with its string of attacks designed to embarrass the FBI, this time claiming to have breached the network of ManTech International, the FBI's cyber-security contractor. - As
promised, Anonymous has sought to embarrass the FBI with a network attack, this
time going after defense contractor ManTech International.
quot;Hacktivist quot;
collective Anonymous claims to have quot;owned quot; the defense contractor
ManTech International and promised to release the sto...
Anonymous continued with its string of attacks designed to embarrass the FBI, this time claiming to have breached the network of ManTech International, the FBI's cyber-security contractor. - As
promised, Anonymous has sought to embarrass the FBI with a network attack, this
time going after defense contractor ManTech International.
quot;Hacktivist quot;
collective Anonymous claims to have quot;owned quot; the defense contractor
ManTech International and promised to release the sto...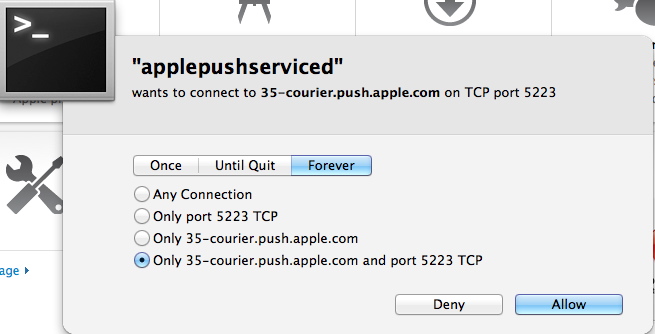 When Lion first appeared in the Apple App store most of probably blindly click YESYES YES ...(more)...
When Lion first appeared in the Apple App store most of probably blindly click YESYES YES ...(more)...  Strong demand in Symantec's backup, data archiving, data loss prevention and security offerings pushed revenue up 15 percent to $1.65 billion. - Data protection and software management
provider Symantec beat Wall Street analyst expectations for its fiscal first
quarter thanks to strong performance from its security and data storage
business lines.
Symantec July 27 reported net income of
$172 million, or 22 cents a share, for the fiscal ...
Strong demand in Symantec's backup, data archiving, data loss prevention and security offerings pushed revenue up 15 percent to $1.65 billion. - Data protection and software management
provider Symantec beat Wall Street analyst expectations for its fiscal first
quarter thanks to strong performance from its security and data storage
business lines.
Symantec July 27 reported net income of
$172 million, or 22 cents a share, for the fiscal ... News Analysis: Even if law enforcement organizations arrested everyone in Anonymous and LulzSec tomorrow, it really wont solve the problem of network intrusions, botnets and attacks. - The FBI and Scotland Yard should be praised in their ability to
track down, identify and arrest members of the related hacking
organizations Anonymous and LulzSec.
The cyber-sleuthing they did is not easy. When you have to do it well
enough for the arrest to hold up in court, its harder still.
...
News Analysis: Even if law enforcement organizations arrested everyone in Anonymous and LulzSec tomorrow, it really wont solve the problem of network intrusions, botnets and attacks. - The FBI and Scotland Yard should be praised in their ability to
track down, identify and arrest members of the related hacking
organizations Anonymous and LulzSec.
The cyber-sleuthing they did is not easy. When you have to do it well
enough for the arrest to hold up in court, its harder still.
... Microsoft has expanded its malware research operations in Munich, Germany, to analyze and detect ongoing cyber-threats. - The latest member of the
Microsoft Malware Protection Center family is open and fully operational in
Germany, according to Microsoft.
The new malware research
facility is in Munich and will monitor threats in the region,
Microsoft said July 26. The facility will be looking at both active threat...
Microsoft has expanded its malware research operations in Munich, Germany, to analyze and detect ongoing cyber-threats. - The latest member of the
Microsoft Malware Protection Center family is open and fully operational in
Germany, according to Microsoft.
The new malware research
facility is in Munich and will monitor threats in the region,
Microsoft said July 26. The facility will be looking at both active threat... The Microsoft Malware Protection Center reported that it found a new Mac backdoor. However, it appears Intego and Kaspersky had already found it. - Microsoft researchers uncovered a new piece of Mac malware
that can install remote-control backdoors on compromised machines. Other
researchers questioned whether it was a credible threat at this time.
Microsoft researchers came across the backdoor, named Olyx,
in a package which contained a dif...
The Microsoft Malware Protection Center reported that it found a new Mac backdoor. However, it appears Intego and Kaspersky had already found it. - Microsoft researchers uncovered a new piece of Mac malware
that can install remote-control backdoors on compromised machines. Other
researchers questioned whether it was a credible threat at this time.
Microsoft researchers came across the backdoor, named Olyx,
in a package which contained a dif... Facebook caves to privacy pressures from Connecticut Attorney General George Jepsen and others by running ads to let users opt out of the tag-suggestions facial-recognition feature. - Facebook July
26 said it has made it easier for subscribers to opt out of a controversial
feature that uses facial-recognition technology to tag users in photos.
Connecticut Attorney
General George Jepsen is taking credit for the change, which includes deleting
the facial-recognition data of us...
Facebook caves to privacy pressures from Connecticut Attorney General George Jepsen and others by running ads to let users opt out of the tag-suggestions facial-recognition feature. - Facebook July
26 said it has made it easier for subscribers to opt out of a controversial
feature that uses facial-recognition technology to tag users in photos.
Connecticut Attorney
General George Jepsen is taking credit for the change, which includes deleting
the facial-recognition data of us... This article discusses disk encryption in view of Microsoft's Bitlocker, and Microsoft Bitlocker Administration and Monitoring (MBAM) solution.
This article discusses disk encryption in view of Microsoft's Bitlocker, and Microsoft Bitlocker Administration and Monitoring (MBAM) solution. Despite the increase in volume and sophistication of cyber-attacks, government officials testified before a U.S. House subcommittee that the country has been slow to beef up IT security. - While
cyber-attacks against U.S. computer networks are becoming more frequent and
increasingly more sophisticated, the country is lagging in its efforts to beef
up IT security, government officials testified in front of Congress.
The
Energy and Commerce Subcommittee on Oversight held hearings ...
Despite the increase in volume and sophistication of cyber-attacks, government officials testified before a U.S. House subcommittee that the country has been slow to beef up IT security. - While
cyber-attacks against U.S. computer networks are becoming more frequent and
increasingly more sophisticated, the country is lagging in its efforts to beef
up IT security, government officials testified in front of Congress.
The
Energy and Commerce Subcommittee on Oversight held hearings ... Security researchers managed to obtain passwords saved on the Mac while in sleep mode using a FireWire device. The issue exists in both Mac OS X "Snow Leopard" and "Lion." - It
is possible to recover user passwords from Mac systems set on sleep mode,
including running the latest version of Mac OS X quot;Lion, quot; a password
recovery software vendor said.
Passware
researchers were able to recover passwords by connecting to a Mac through the
FireWire port, the co...
Security researchers managed to obtain passwords saved on the Mac while in sleep mode using a FireWire device. The issue exists in both Mac OS X "Snow Leopard" and "Lion." - It
is possible to recover user passwords from Mac systems set on sleep mode,
including running the latest version of Mac OS X quot;Lion, quot; a password
recovery software vendor said.
Passware
researchers were able to recover passwords by connecting to a Mac through the
FireWire port, the co... Apple released a new Mac OS 10.6.8 software update for "Snow Leopard" to address problems an earlier update caused. - Less than a week after Apple's
new Mac OS X quot;Lion quot; made its debut, it released a software update to
resolve problems from an earlier update and provided three security updates.
Mac OS X 10.6.8 resolved
some issues that arose after quot;Snow Leopard quot; users applied the earlier
upd...
Apple released a new Mac OS 10.6.8 software update for "Snow Leopard" to address problems an earlier update caused. - Less than a week after Apple's
new Mac OS X quot;Lion quot; made its debut, it released a software update to
resolve problems from an earlier update and provided three security updates.
Mac OS X 10.6.8 resolved
some issues that arose after quot;Snow Leopard quot; users applied the earlier
upd...
 The director of US-CERT, a division of the Department of Homeland Security has resigned amidst a surge in the number of cyber-attacks on government agencies and private contractors. - The director of the United States Computer Emergency
Response Team resigned last week without any official explanation.
Randy Vickers resigned July 22, effective immediately,
according to an email to employees sent by Roberta Stempfley, acting assistant
secretary at Department of Homeland Securi...
The director of US-CERT, a division of the Department of Homeland Security has resigned amidst a surge in the number of cyber-attacks on government agencies and private contractors. - The director of the United States Computer Emergency
Response Team resigned last week without any official explanation.
Randy Vickers resigned July 22, effective immediately,
according to an email to employees sent by Roberta Stempfley, acting assistant
secretary at Department of Homeland Securi... China has always been known for counterfeiting high-end luxury brands. But not content to pirate software or copy phones, entrepreneurs have now cloned the entire Apple Store. - Chinese
officials closed two unauthorized Apple stores for operating without a proper
business license, according to news reports. However, three other fake Apple
stores were allowed to remain open because they had proper local permits.
As
part of a probe of more than 300 IT businesses, the Kun...
China has always been known for counterfeiting high-end luxury brands. But not content to pirate software or copy phones, entrepreneurs have now cloned the entire Apple Store. - Chinese
officials closed two unauthorized Apple stores for operating without a proper
business license, according to news reports. However, three other fake Apple
stores were allowed to remain open because they had proper local permits.
As
part of a probe of more than 300 IT businesses, the Kun... When it comes to security, specifically when it comes to vulnerability management, one size doesn’t fit all. Organizations need to customize their tools based on a wide variety of business requirements. These include everything from scan windows, frequently changing credentials, report distribution and most importantly the architecture and volume of data that needs to be [...]
When it comes to security, specifically when it comes to vulnerability management, one size doesn’t fit all. Organizations need to customize their tools based on a wide variety of business requirements. These include everything from scan windows, frequently changing credentials, report distribution and most importantly the architecture and volume of data that needs to be [...] I’m really starting to enjoy the “odd” months, Microsoft kept to their pattern and released only four security bulletins today. A welcome reprieve from last month’s sixteen bulletins. The only “Critical” rated vulnerability released today affects the Windows Bluetooth 2.1 stack. This particular vulnerability is somewhat interesting due to the attack vector. As you know, [...]
I’m really starting to enjoy the “odd” months, Microsoft kept to their pattern and released only four security bulletins today. A welcome reprieve from last month’s sixteen bulletins. The only “Critical” rated vulnerability released today affects the Windows Bluetooth 2.1 stack. This particular vulnerability is somewhat interesting due to the attack vector. As you know, [...] At eEye we have been continuing an aggressive release schedule of major product updates that simplify your vulnerability management and compliance process. One of the ways that we continue to simplify vulnerability management is through new capabilities and reporting that allow for better prioritization of vulnerabilities from an overall risk management perspective. While other products [...]
At eEye we have been continuing an aggressive release schedule of major product updates that simplify your vulnerability management and compliance process. One of the ways that we continue to simplify vulnerability management is through new capabilities and reporting that allow for better prioritization of vulnerabilities from an overall risk management perspective. While other products [...] Call for Papers IEEE Security & Privacy Software Static Analysis Abstract submissions due: 15 Aug. 2011 Final submissions due: 15 Sept. 2011 Publication date: May/June 2012 Secure and reliable software is hard to build, but the costs of failure are steep. Data breaches caused by attackers exploiting vulnerabilities in software made many headlines in 2011 [...]
Call for Papers IEEE Security & Privacy Software Static Analysis Abstract submissions due: 15 Aug. 2011 Final submissions due: 15 Sept. 2011 Publication date: May/June 2012 Secure and reliable software is hard to build, but the costs of failure are steep. Data breaches caused by attackers exploiting vulnerabilities in software made many headlines in 2011 [...] Rich Mogull talks about real world IT security challenges today in his column, “Simple Isn’t Simple” in Dark Reading. I agree 100%. One of the Rich’s points is security has to scale or it doesn’t solve the real world problem. In most cases we know how to solve a security problem for a single instance [...]
Rich Mogull talks about real world IT security challenges today in his column, “Simple Isn’t Simple” in Dark Reading. I agree 100%. One of the Rich’s points is security has to scale or it doesn’t solve the real world problem. In most cases we know how to solve a security problem for a single instance [...] Sometimes the simplest things make the biggest difference. A few weeks ago, I published a blog on Metasploit Integration and have had multiple inquiries on similar types of integration. First, I would personally like to thank the Core Security team for providing evaluation licenses and integration into Core Impact. Second, a big thank you for [...]
Sometimes the simplest things make the biggest difference. A few weeks ago, I published a blog on Metasploit Integration and have had multiple inquiries on similar types of integration. First, I would personally like to thank the Core Security team for providing evaluation licenses and integration into Core Impact. Second, a big thank you for [...] In this article I am going to discuss some of the things that need to be taken into consideration when building a malware analysis lab.
In this article I am going to discuss some of the things that need to be taken into consideration when building a malware analysis lab.